FluidAttack
| Scanning Tool | Web |
Mobile |
Local |
API |
Extension |
Serverless |
Instructions |
|---|---|---|---|---|---|---|---|
FluidAttacks Free & Open Source CLI |
Leverage FluidAttacks open source CLI to perform automated static (SAST) scans against your application. A Docker image has been created to include all necessary CWEs. Simply spin up the container and run the scan command within it. |
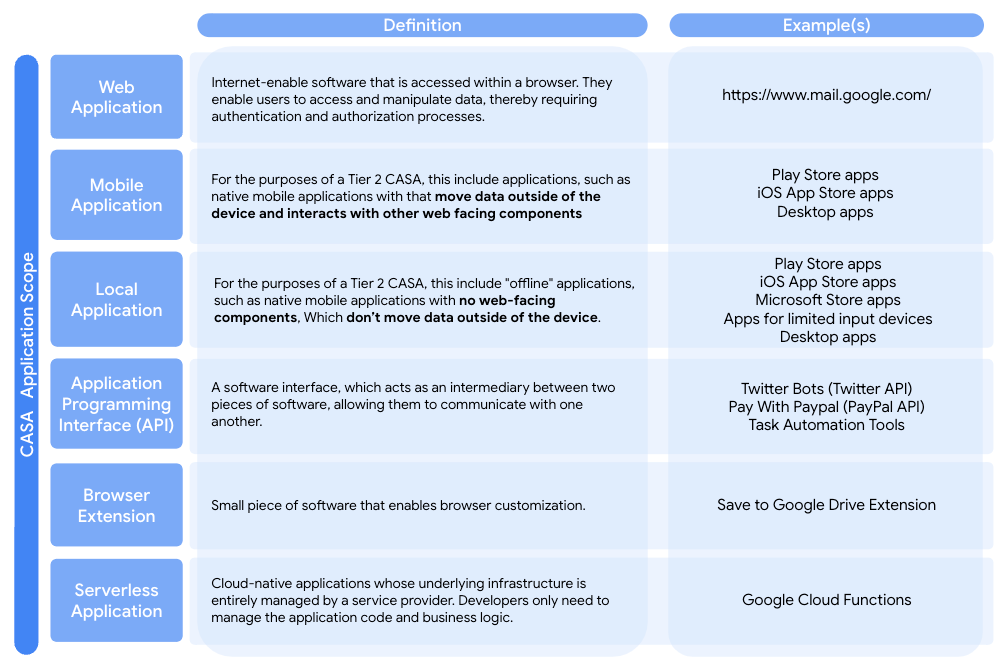
For definition of each type
Click here
A scan the source code of your Web, Mobile, or Internal Applications, Browser Extensions, or Serverless Functions can be performed following the below steps:
-
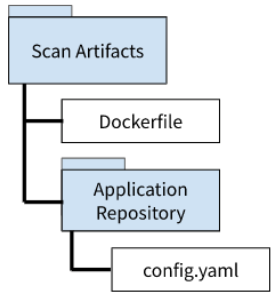
Create a folder to contain the scan artifacts.
-
Name the folder and upload the CASA scan Dockerfile
-
Clone the application repository within this folder and add the config.yaml file within the root folder. This file can be found here: config.yaml
-
The final setup should appear as such:
The following application types have additional packaging considerations. Please follow the necessary format for a successful scan.
Android Studio Projects: AndroidManifest.xml must be located at ‘app/src/main/AndroidManifest.xml’ and the directory ‘app/src/main/java/’ must exist.
-
The configuration file (config.yaml) specifies where your scan results will be stored. The default values are shown here.
If you are scanning a native Android application, specify the location of any APKs by updating the following within the configuration file:
apk:
# Description: dynamic scan of Android APKs.
include:
-
app-arm-debug-Android.apk
-
app-arm-Android.apk
Update the “include” parameters with the file paths to your target APKs relative to the location of your config.yaml file.
-
output:
file_path: ./Fluid-Attacks-Results.csv
format: CSV
Keep the format as CSV, but feel free to change the name of the output within the config.yaml file.
-
Build the docker image by running the below command:
docker build -t casascan /path/to/Dockerfile
-
Start the container and initiate a Fluid SAST scan by running the below command (note this step will take a while to complete):
docker run casascan m gitlab:fluidattacks/universe@trunk /skims scan {App Repo Name}/config.yaml
-
Once Step 5 is completed, the results will be stored in a CSV file within your application repository folder.
-
After the scan is complete, obtain the ID of your container by running docker ps and copying the port value
-
Copy the scan results to your host by running below command:
docker cp {Container ID}:/usr/scan/{App Repo Name}/Fluid-Attacks-Results.csv SAST-Results.csv